Hey Chrazey,
I can shed some light on this, I have extensively used ToR in my line of work and in my personal time have ran many Relays and Exit Nodes.
Firstly. The Dark Web / Deep Web are incorrectly stated as "ToR" However, anything that is referred to the aforementioned is anything that isn't indexed by a search engine, such as Google (Surface Web).
Did you know that the surface web makes up for a relatively small fraction of what the internet holds? Think about that for a second.

A lot of information on the deep web is accessible without the need for ToR - You just need to be able to find it as it isn't indexed.
ToR
ToR - The Onion Router as it's called is a low-latency anonymity network that is ran by world wide volunteers such as myself and funded by donations with a small percentage by the US Navel Research Laboratory.
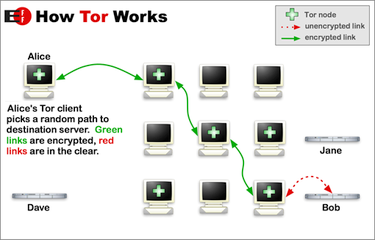
The reason why it's called The Onion Router is because of how it works:
You have what is called Nodes. They are comprised of Entry Node, Middle Relay Nodes and an Exit Node.
On a standard configuration, you usually connect to around 3 or 4 of these Nodes. One Entry Guard/Node > 2 Middle Relay > Exit Node
A graphic to demonstrate this is below:
This is called a ToR Circuit.
Each packet of information you send trough this network has been encrypted with layers of encryption. Each Node decrypts one layer of of encryption and it is then passed on to the next node (Middle Relay) and that decrypts the next layer of encryption and so fourth until it reaches the exit relay.
The exit relay is the final node in the circuit. This node decrypts the final layer of encryption before it is passed to the destination address (oc3d.net) for example. This exit relay is what you will appear to reside from and is the address of which server administrators will see.
Once a ToR Circuit has been established, the relays and exit nodes do not have any knowledge of your real IP Address. This is due to the fact that once you are connected to the ToR network, after the first part of the traffic is sent to the next middle relay, the next middle relay only has IP information of the previous middle relay and so fourth, catch my drift?
The purpose of this is to masquerade traffic origin. I can trace the exit node perfectly fine, but from then on it is futile to trace back further as the ToR Relays has no knowledge of the origin IP and the client rebuilds ToR Circuits to maximize anonymity and to reduce traffic correlation attacks.
Unfortunately, as the Exit Relay is the final piece in the jigsaw and finishes the decryption of the packet, it is therefore able to see everything that the user is doing. However, with the nature of the ToR network it is unable to tell who.
The ToR Network is very safe in terms of remaining anonymous. You hear of these news stories about how the FBI etc have been able to track users. Well this is because of client side attacks. That person was a little silly and either divulged personal information or did not use the ToR Browser Bundle. You can use any browser with the ToR network, but you must be able to configure it correctly, The ToR Browser Bundle is actually pretty good. The clientside attacks I am referring to are Javascript based attacks etc. When I visit a website, cookies and caches are stored for example. Most users got caught because what happened is that they used ToR did what they did but then used that same browser to browse the internet without ToR and as such those cookies/javascript/etc phoned home and thus revealed the true IP of that user.
To prevent this type of attack, Tails is highly recommended if you are unsure on how to properly protect yourself.
With regards to the web browsers and ToR. Web Browsers are clients used to parse the WWW. ToR is a network that is used to connect to using the ToR Client. You are able to browse the WWW and .onion sites. Onion sites are websites that only reside on the ToR Network, and as such you need to connect to that network to be able to access them. Although, you can get ToR2Web services which proxy ToR to the Clearnet.
The ToR Network is the ideal place for uncensored content, as it's hard to track and trace origin servers that host this content as they work and host content in the same way as how ToR user connects.
I can go more in depth with regards to ToR, but I tried to keep it as high level as possible for you to understand.
I have written an an easy to follow guide that you can read in order to help protect tracking online and regain some privacy online using Firefox.
https://infosecdroogs.co.uk/privacy-on-the-web/